Microsoft developed a new Defender for Endpoint (MDE) security feature to help enterprises prevent attackers and malware from using unmanaged devices over the network.
In the event that a computer is compromised or there is a suspicion of malware, this new feature allows administrators to "contain" unmanaged Windows devices on their network.
Once labeled as "content," the security platform will instruct Windows systems on the network to block all communications to the device that is "content."
This prevents malicious actors from moving laterally within the organization using unmanaged devices and prevents the spread of an infection that would otherwise cause further damage.
"This action can help prevent neighboring devices from being compromised while the security operations analyst locates, identifies and remediates the threat on the compromised device," Microsoft explains.
However, there is a limitation: the new MDE capability only works with embedded devices running Windows 10 and later or Windows Server 2019 and later.
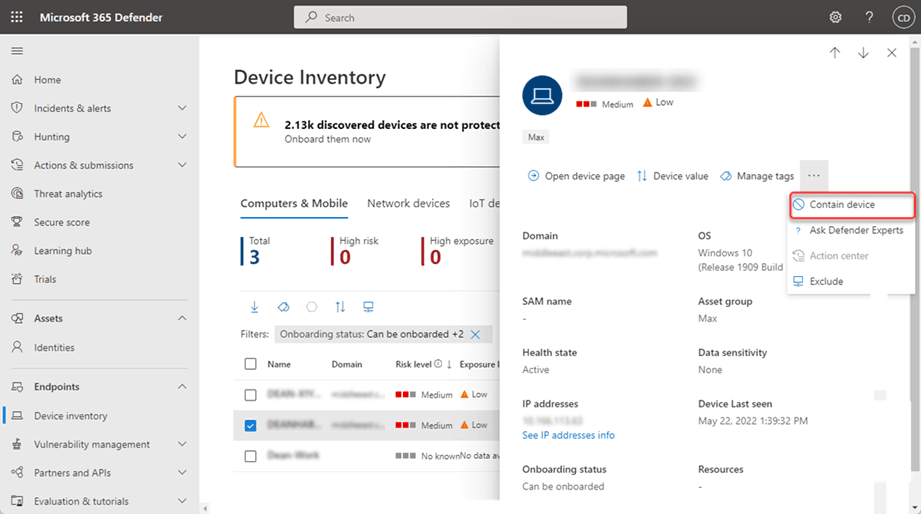
After containing an unmanaged device, it can take up to 5 minutes for Microsoft Defender for Endpoint embedded devices to begin blocking communications.
If any of the devices on the network change their IP address, all enrolled devices will recognize it and begin blocking communications with the new IP address.
In short, Microsoft Defender has released a new and interesting feature. Network administrators will be able to isolate devices that have been hacked, or there are suspicions that they may pose a danger to the security of other computers connected to the network and action must be taken.
Likewise, it is always advisable to take precautionary measures. A clear example is maintaining security when working in the cloud. This will prevent other devices from being compromised by a computer attack.
Edward Ustariz
Technology Support Engineer
